Discover Global System Analysis for Security Operation Center
An AI-Driven SoC Solution
our R&D Native & modular 360° Ai-SecOps Solution
BACKGROUND
NKINDA GSA SOC is a revolutionary AI-driven operational security platform that redefines threat management through intelligent automation. By integrating AI into security operations workflows, we offer a proactive, automated approach to threat detection, investigation and response (TDIR).
Our Security Operation Center (SOC) combines the power of AI with advanced automation to monitor, analyze and respond to threats in real time, ensuring complete and uninterrupted protection of our customers' systems. With NKINDA GSA SOC, you gain access to the most advanced security solution on the market, capable of adapting to evolving threats and continuously protecting your critical assets.
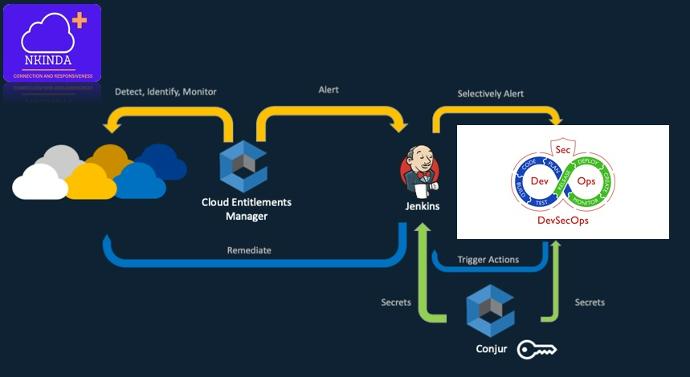
NKINDA GSA SOC is positioned as the ultimate solution
for managing current and future security challenges. With a unique combination of AI-driven technologies, advanced automation and powerful features, we offer our customers 360° protection in an ever-changing digital world.
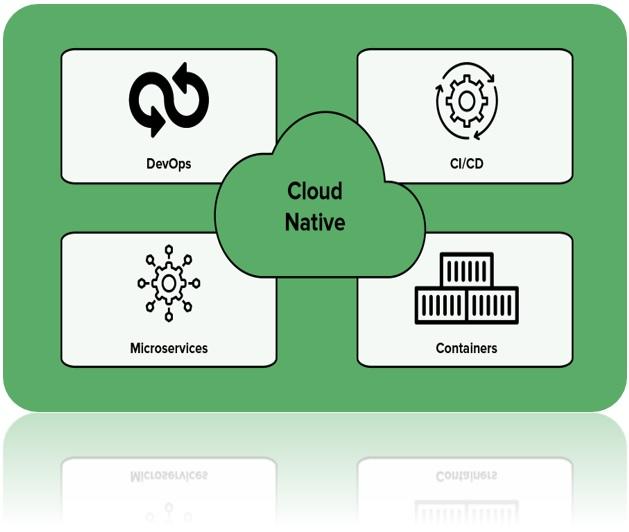
Cloud-native Architecture
NKINDA GSA SOC is designed to take full advantage of the cloud. This cloud-native architecture ensures maximum flexibility, automatic scalability and seamless integration into hybridand multi-cloud environments, giving you unified protection wherever your assets are.
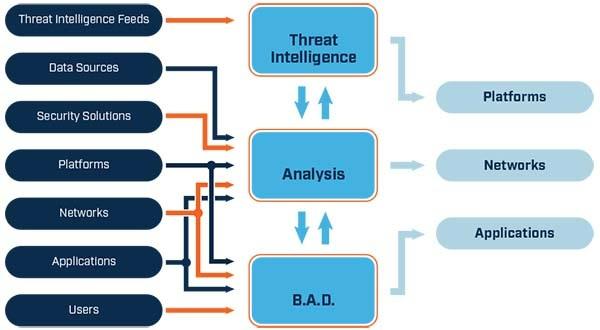
Security Log Management
Security log management is central to our solution. NKINDA GSA SOC collects, aggregates and analyzes security logs from all your infrastructures, giving you centralized visibility and actionable information to prevent attacks before they happen.
Open and Extensible Platform
Our platform is open and extensible, allowing you to easily connect the tools you already use. NKINDA GSA SOC supports hundreds of products, both on-premise and in the cloud, as well as various data transport protocols (APIs, agents, syslog, SIEM). This flexibility ensures seamless integration into your existing environment.

Prescriptive, Outcomes-focused Use Case Coverage
We don't just react to incidents. NKINDA GSA SOC provides prescriptive, outcomes-focused use case coverage. Our algorithms are designed to anticipate threat scenarios and propose preconceived solutions for maximum efficiency.

Automated Investigation Experience
NKINDA GSA SOC's Automated Investigation Experience speeds up the investigation process by automatically gathering relevant information on security incidents. This feature saves valuable time and significantly improves the speed and accuracy of responses.
Powerful Behavioral Analytics
Our advanced behavioral analytics detect even subtle anomalies and suspicious behavior within your systems. Thanks to this analysis, NKINDA GSA SOC identifies internal and external threats before they become critical, ensuring proactive protection of your assets.
Nkinda AISecOps Module: Reinforcing Use Cases with AI/Machine Learning
This feature harnesses the power of AI/Machine Learning to continuously improve security use cases. Nkinda AISecOps Module enable an automatic analysis of threat models and the constant evolution of algorithms. It can adapt and refine its attack/cyberdefense scenarios, enabling more accurate detection of emerging threats.
AI/Machine Learning: by learning from past incidents and behaviors, improves the accuracy of detections and automated responses. This ensures that your security infrastructure is always up-to-date and proactive in the face of new threats, while reducing false positives. With this advanced capability, you benefit from a dynamic, scalable defense that adapts to changes in the digital environment and the growing sophistication of cyberattacks.
Interoperability
The solution will ensure ease of use and integration across all various IT domains, including it also comes along with portable executable files.
• IT INFRASTRUCTURE
• CORE NETWORK
• RAN (Radio Access Network)
• PACKET SWITCHING
• INTELLIGENT NETWORK
• VALUE ADDED SERVICES
• IP / DATACOMMS NETWORKS
This interoperability will allow seamless integration and usage across different technological environments and systems in all domains
Orchestration
The solution will support task and process orchestration to facilitate bulk system changes, ensuring:
• Automated deployment and configuration management.
• Consistent and error-free updates across multiple systems.
• Streamlined processes for large-scale changes and migrations.
DEVELOPMENT / INTEGRATION PROCESSES
Week 1
- Audit & analysis of existing
situation
- Identification & elaboration of
requirements.
Week 2
Start of dev /+ integration
weekend delivery.
Week 3
Validation tests & Delivery
###
Evaluation &
observation
TREE (3) WEEKS of DEV / Core Module

Success Stories-Telecom
-Performance analysis of web services
-Online Charging System integration support
-Collect & provide tuning LOG Tshoot Analysis
-Integration on Open service Gateway
- Integration support for Backbone IP/MPLS
-
Integration support for Core Network

Intregration of Nkinda GSA SOC
Three Possibilities of deployment
- portable software
- On premise SaaS
-
Cloud SaaS
Hardware specification
8 core CPU
32 GB RAM
Disk: 2 Tera

Contracts and confidentiality
NDA
:Confidentiality agreement
Sale of software licenses
Technical support contract

Phased approach
The implementation will follow a phased approach:
• Phase 1: Assessment and Planning - Assess current systems in all domains, define requirements, and plan implementation.
• Phase 2: Integration and deployment – integration and deployment of the site reliability solution software across all domains.
• Phase 3: Testing and Validation - Conduct rigorous testing to validate functionality and performance.
• Phase 4: Training and Continues Integration and Deployment - Train staff and deploy the solution across the organization.
• Phase 5: Monitoring and Optimization - Monitor performance and optimize the solution based on feedback

Expected Outcome
• Improved System Availability - Achieve near 100% uptime.
• Efficient Fault Management- Faster detection and resolution of issues.
• Enhanced Performance Monitoring - Real-time insights into system performance.
• Proactive Incident Management - Predict and prevent potential incidents.
• Continuous Improvement - Leverage historical data for ongoing optimization.
• Seamless Interoperability - Smooth integration across various IT domains.
• Effective Orchestration - Simplified bulk system changes.
• Optimized Network Planning - Data-driven network design and optimization.
• Comprehensive Performance Analysis - Real-time monitoring and KPI tracking with visualization tools.
Critical GSA SOC Solution Operational KPI
The solution will address several crucial SRE operational KPIs to ensureoptimal performance andreliability, including:
• Mean Time to Detect (MTTD): The average time taken to detect an incident. Reducing MTTD helps in quicker identification of issues.
• Mean Time to Resolve (MTTR): The average time taken to resolve an incident after it has been detected. Lower MTTR indicates faster resolution capabilities.
• Service Level Indicators (SLIs): Metrics that measure the performance of a service (e.g., latency, error rate, throughput).
• Service Level Objectives (SLOs): Targets set for SLIs that define acceptable performance levels.
• Service Level Agreements (SLAs): Formal agreements that set expectations for service performance between service providers and customers.
• Change Failure Rate: The percentage of changes that result in degraded service or require remediation. Lower rates indicate more successful changes.
• Error Budget:The allowable amount of downtime or errors within a specific period, derived from SLOs.
• Incident Rate: The frequency of incidents occurring within a specific timeframe. Monitoring this helps in understanding system stability.
• Availability: The percentage of time the system is operational and available. High availability is crucial for user satisfaction.

Evaluation Criteria
The success of the PoC will be evaluated based on:
• System Uptime - Measurement of system availability.
• Alarm Prioritization Accuracy- Reduction in false positives and accurate grading of alarms.
• Fault Resolution Time - Reduction in the time taken to resolve faults.
• User Feedback - Feedback from system administrators and users.
• Performance Metrics - Improvement in key performance indicators (KPIs) such as MTTD, MTTR, SLIs, SLOs, SLAs, Change Failure Rate, Error Budget, Incident Rate, and Availability.
• Interoperability - Successful integration and usage across various IT/ network domains.
• Orchestration Effectiveness - Efficiency and accuracy of bulk system changes with zero tolerance to downtime
• Network Planning Optimization - Quality of insights and improvements in network planning.
• Visualization and Analysis - Effectiveness of real-time monitoring and KPI tracking through visualization tools
